When it comes to securing your mobile app, one of the main challenges you'll face is the wide range of mobile devices it will be installed on.
After all, while you can control the security protections in your own digital products, you have very limited visibility over the smartphones of those who’ll be using them. All the pen testing, debugging, and QA analysis in the world can’t guarantee your app will make its way onto an up-to-date and uncompromised device.
One of the biggest examples of this issue is rooting and jailbreaking. With a standard iOS or Android device, you can rely on several out-of-the-box defenses designed to protect apps, data, and users. But when smartphones are rooted or jailbroken, these defenses become weaker, and sometimes entirely redundant.
This is why app developers want to protect the integrity of their apps by detecting rooted or jailbroken devices. But that’s more difficult than it seems.
So how can you get it right? What are the most effective root/jailbreak detection tools today? And what’s the best approach for developers like you looking to protect their valuable intellectual property?
In this article, we explain everything you need to know about root/jailbreak detection for mobile apps.
What is rooting/ jailbreaking? Recapping the basics
Rooting or jailbreaking removes built-in restrictions on mobile devices, giving the end user admin-level permissions to make changes to their device. Rooting occurs on Android devices, and jailbreaking on iOS.
But rooting and jailbreaking aren’t new. Mobile users have been using these techniques to remove smartphone controls for as long as manufacturers have been implementing them. As new rooting/jailbreaking techniques emerge, identifying such devices only grows more difficult.
Read more: Root detection: What it is and how it works
Why do people root or jailbreak devices?
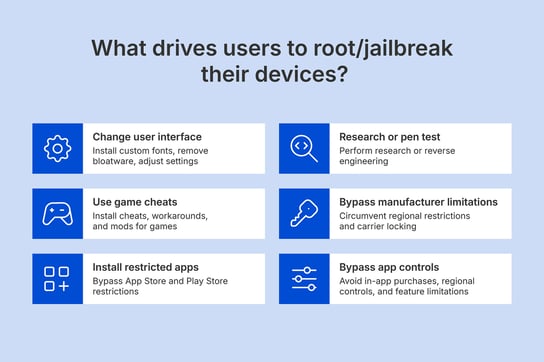
Sometimes, rooting or jailbreaking is done directly by malicious actors. But usually, the mobile device owners perform it. There are many reasons they might do it:
- User interface: Users may wish to change default device settings, like installing custom fonts, removing bloatware, or changing other settings.
- Game cheats: Elevated permissions allow end users to install cheats, workarounds, and mods for games on their mobiles.
- Installing apps: Most iOS devices only let you install apps from the App Store, and Android devices from Google Play Store. End users avoid these restrictions by jailbreaking.
- Security/pen testing: Security researchers and hackers often need admin rights to perform security research. This can be either for legitimate reasons (like pen testing) or malicious ones (like reverse engineering).
- Manufacturer limitations: Users may choose to jailbreak devices to circumvent manufacturer limitations like regional restrictions and carrier locking.
- App controls: Rooted/jailbroken devices also allow users to get around app-specific restrictions, including in-app purchases, regional controls, feature limitations, and more.
The danger of rooting/jailbreaking
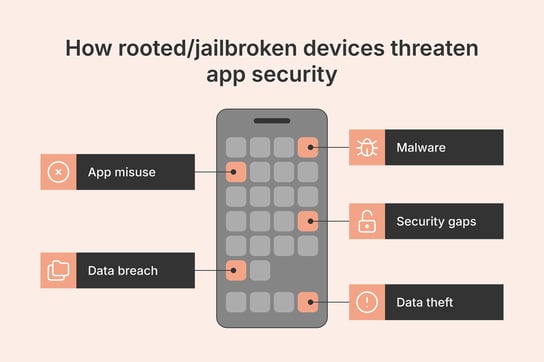
Whatever the reason for rooting/jailbreaking, such devices come with their own challenges, particularly organizations whose apps are downloaded and run on them. These include:
- Malware: Rooted and jailbroken devices are more susceptible to malware than standard mobile devices. While jailbreaking/rooting tools generally try to keep malware protections intact, this isn’t always possible. So, there is an increased risk of malware infecting your apps via freeware or decoy/repackaged apps.
- Vulnerabilities: Jailbroken devices can’t receive software updates because successful jailbreaking relies on exploiting vulnerabilities. This is why jailbroken iOS devices will almost certainly end up accumulating software vulnerabilities over time. This is less of an issue on Android devices because rooting doesn’t usually involve vulnerabilities.
- App misuse: End users can use jailbreaking/rooting to misuse apps, particularly gaming/streaming ones for which providers need to build rules around gameplay, regional restrictions, and in-app purchases.
- Data breach: Admin-level rights also make it easier for malicious actors to steal sensitive app data because jailbreaking/rooting removes the sandboxes designed to prevent data from leaving apps. This creates a security and compliance risk for app vendors.
- Loss of sensitive information: Hackers use rooted/jailbroken devices to analyze the app during runtime to reverse engineer an app’s internal logic. This risks code injection, repackaging, vulnerability exploitation, and other issues.
In short, app manufacturers have reasons to be wary of rooted/jailbroken devices, especially for apps involving sensitive personal data that needs to be protected, like financial services apps.
The good news is there are several techniques and tools that can help you detect rooted/jailbroken devices. But the bad news is: it isn’t as simple as it may first appear.
How jailbreaking and root detection works
Rooting and jailbreaking might not be new—but neither are attempts to detect them. Over the years, this has created a cat-and-mouse game between those attempting to unlock their devices and the tools designed to detect this. In this section, we discuss some of the most common methods, considering the pros and cons of root detection and jailbreaking, and what other options are available.
Today, there are several common techniques. The app includes these features in its code, which activate on a user’s device when the app is installed. While these techniques aren’t perfect, they create an effective first layer of defense that can reduce your app’s exposure to rooted/jailbroken devices.
Here are some of the most common jailbreaking/ root detection methods:
- Identifying jailbreaking/root management apps: End users install these apps to easily root or jailbreak their own devices. So, the presence of these apps generally indicates a rooted/jailbroken device, like:
Android: SuperSU, Magisk Manager, KingRoot
iOS: Cydia, Sileo, Zebra - Scanning device files: Rooting/jailbreaking tools often create specific files on the device, including packages, binaries, and directories. Identifying these files is one of the most common ways to detect elevated privileges on a device.
Android: Files like Superuser.apk and /system/xbin/su, packages like eu.chainfire.supersu and com.topjohnwu.magisk, and binaries like /system/bin/su binary. Many of these are specific to the rooting tool used, in this case, SuperSU and Magisk Manager.
iOS: Examples tend to be specific to the jailbreaking tool used, including: /private/var/tmp/cydia.log, /Applications/Cydia.app, /etc/apt, /usr/bin/sshd, /var/cache/apt. On iOS, particular binaries like “bash” and “sshd” are often present on jailbroken devices. - Detecting hooking frameworks: Hooking frameworks are used to alter an app’s behavior during runtime. This requires elevated privileges, so finding evidence of these hooking frameworks is another common rooting/jailbreak detection technique.
- Sandbox inspection: (iOS only) Standard iOS devices feature strong sandboxes to prevent sensitive information from leaving apps and to restrict the access that apps have to information on the wider device. Testing the integrity of sandboxes is an effective jailbreak detection method. It generally involves checking to see if you can access files that the sandbox would ordinarily restrict access to.
- Analyzing build or system properties: (Android only) Properties like ro.build.tags, ro.build.type, ro.debuggable, ro.secure, and ro.mock.location are often altered on rooted devices. If these deviate from a typical Android device, it could signal rooting.
When your app discovers evidence of rooting/jailbreaking, there are several options for how you can proceed:
- Issuing a warning to the end user
- Blocking access to particular features
- Blocking access to server-side resources
- Terminating the app entirely
- Notify the server to ban the user account
Generally, root/jailbreak detection tools allow app manufacturers to customize these responses so you can choose what the best response is for your app and data.
Some of the techniques we described in this chapter are easier to bypass than others. When rooting/jailbreaking is performed through pre-packaged apps by non-technical users, root detection can be quite effective. But as we’ll discover, this isn’t always the case.
Read more: Mobile app security basics: Understanding hooking frameworks
The Promon view: Root detection is a nice-to-have
“No root/jailbreak detection is perfect. They just add a useful hurdle for malicious actors to navigate. But there will always be ways to get around them. That’s why you shouldn’t base all your security on rooting detection. You need to add other protections in your app.”
While many jailbreak/root detection strategies have emerged over the years, hackers have developed innovative ways to get around them. This cat-and-mouse game means many of the root/jailbreak detection techniques we used to rely on simply aren’t effective anymore.
The methods we discussed in the last section are still commonly used in today’s rooting/jailbreaking tools. But they aren’t foolproof:
- Sophisticated methods: Rooting/jailbreaking tools are getting more sophisticated and are often able to hide their presence and activity.
- Elevated privileges: By definition, rooting/jailbreaking gives the end user elevated privileges, which can be used to disable detection tools.
- Multiple tools: For a user, getting admin rights on a device can be as simple as using tools like SuperSU which are easy to detect, or as complex as creating their custom Android kernel, which renders most root detection techniques ineffective.
- False positives: Jailbreak/root detection tools can create false positives. At the same time, the variety of device vendors and models on Android means there’s no 100% effective way of distinguishing between rooted and non-rooted devices.
- Ever-tightening sandboxes: Apple and Google have tightened sandboxes over time for data privacy reasons, which limits an app’s ability to monitor activity, files, and the presence of other apps on the device.
Taken together, these challenges mean that no jailbreak/root detection tools can be 100% effective.
So, app manufacturers have a key challenge to deal with: how do you protect your sensitive data and intellectual property from the risks of rooted/jailbroken devices?
At Promon, we take a different approach. Our view is that it’s safer to assume devices are rooted or jailbroken, and work backwards from there.
Effectively, this means defending against the vulnerabilities and challenges that rooting/jailbreaking creates, as well as trying to avoid it in the first place.
After all, rooted/jailbroken devices aren’t inherently more dangerous—they just lay the groundwork for several other potential attacks and vulnerabilities. If we can protect against these more fundamental issues, rooting/jailbreaking detection stops being an absolute necessity and becomes a “nice-to-have.”
A layered approach to mobile app defense
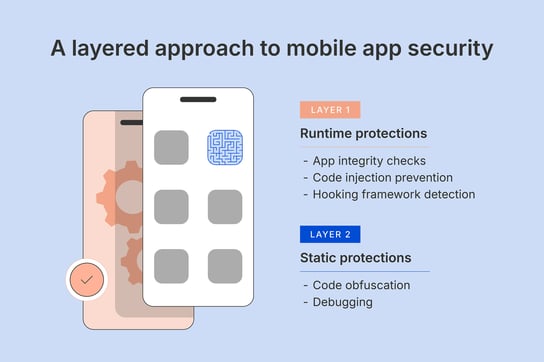
“When it comes to app security, we need to think of it in layers. The first layer is rooting/jailbreak detection, which can identify devices rooted through the common methods.
End users can get around these hurdles but they have to put some effort in and know what they’re doing. That’s why we need to include other defenses like integrity checks, code obfuscation, and more.”
The best approach to app security is a layered one, and root/jailbreak detection techniques can play a valuable role in this strategy, including the techniques we discussed. This is particularly important in regions where root/jailbreak detection is a regulatory requirement.
But even when you have to include detection tools, you shouldn’t stop there. If you want to protect against the issues that rooted/jailbroken devices can create, you need to tackle the more fundamental issues that rooting/jailbreaking can lead to.
This is the approach we take at Promon. We include rooting/jailbreaking detection tools as a standard in our portfolio of app security products. But we also combine this with other tools and techniques:
Runtime protections
These tools help prevent malicious activity like runtime analysis, malware injection, and more, which hackers use to reverse engineer the app logic or alter its behavior during runtime. These protections are a vital part of keeping your app safe:
- App integrity checks: Protect your app’s code and resources to detect any changes made during runtime.
- Code injection prevention: Prevents hackers from inserting malicious code into your app.
- Hooking framework detection: Detects hooking frameworks that try to alter your app’s behavior during runtime.
Static protections
A hacker may also try to perform “on-disk” analysis instead of or in combination with runtime analysis. This can include finding hard-coded tokens, passwords, or keys, as well as identifying vulnerabilities, stealing intellectual property, or other information designed to help plan a runtime-based attack.
Static protections aim to make it as difficult as possible to perform this analysis. These include:
- Code obfuscation: This stops hackers from reverse engineering the logic of your code using techniques that include removing/renaming symbols and names, complicating code logic and control flow, hiding API calls, and obfuscating data and strings.
- Debugging: A variant of code obfuscation, this focuses on removing debug information from the binary. This also helps to stop the attackers from reverse engineering the app to gain knowledge about vulnerabilities, code logic, and other sensitive information.
Taken together, these techniques create a multi-pronged defense strategy that protects your app from both static and runtime-based attack strategies.
Read more: Obfuscation explained: A comprehensive guide to code protection techniques
Where to go from here
Root and jailbreak detection remains a relevant, yet imperfect, aspect of mobile app security. The evolving landscape of rooting/jailbreaking, coupled with increasingly restricted app permissions, necessitates a more comprehensive, layered security strategy. By shifting the focus towards mitigating the underlying risks associated with rooted/jailbroken devices—like code injection, reverse engineering, and data breaches—you can build more resilient applications.
Ultimately, a combination of proactive detection and robust preventative measures offers the most effective approach to safeguarding sensitive data and intellectual property in an increasingly complex mobile environment.



